Configuring a task sequence to enable Bitlocker on Windows 7 with two model laptops:
Dell Latitude E5400
HP ProBook 640 G2
As these need to be wiped clean, and I like to start with a clean slate, I have the following steps defined for helpdesk to perform before beginning the task sequence:
Prepare Dell Latitude E5400
F12
BIOS Setup
Settings
Security
TPM Security
Clear the TPM
Exit (Reboot)
F12
BIOS Setup
Settings
Security
TPM Security
Uncheck “TPM Security”
Exit, saving changes. (Reboot)
Prepare HP ProBook 640 G2
ESC – for Startup Menu
F10 – for BIOS Setup
Security tab
TPM Embedded Security
TPM Device – Hidden
TPM State – unchecked
Clear TPM – On next boot
TPM Activation Policy – Allow user to reject
Exit
Save – Yes
“TPM Ppi” screen
F1 to accept
At this point, the TPM is disabled, inactive, and unowned.
In the task sequence, I check to see if the workstation is a laptop by using the IsLaptop variable.
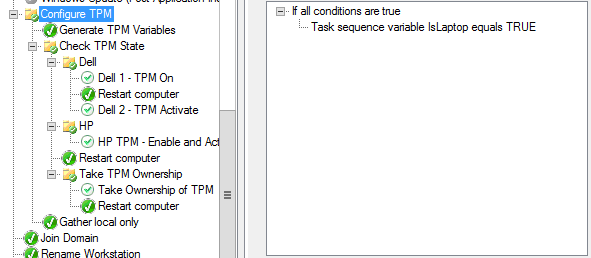
If it is, I then use the ZTICheckforTPM.wsf script (https://blogs.technet.microsoft.com/deploymentguys/2010/12/22/check-to-see-if-the-tpm-is-enabled) to populate the TPMEnabled and TPMActivated variables. I also updated the script to populate the TPMOwned variable.
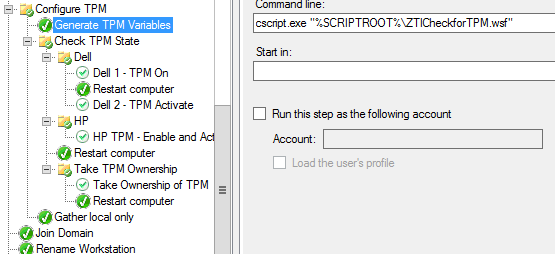
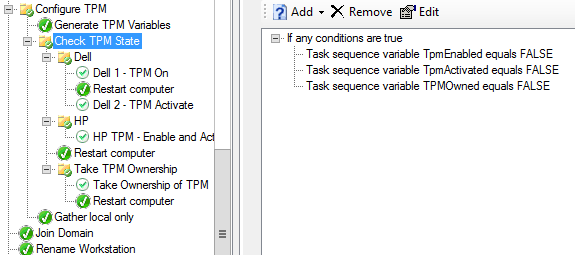
I found the results were inconsistent when trying to enable and activate the TPM in one step on the Dell system, so I broke it out into two (might have been a learing curve, but in any event, here it is). I just defined two applications using the CCTK.EXE:
Application 1: Dell 1 – TPM On
cctk.exe –setuppwd=dell3
cctk.exe –tpm=on –valsetuppwd=dell3
cctk.exe –setuppwd= –valsetuppwd=dell3
Application 2: Dell 2 – TPM Activate
cctk.exe –setuppwd=dell3
cctk.exe –tpmactivation=activate –valsetuppwd=dell3
cctk.exe –setuppwd= –valsetuppwd=dell3
For the HP, the BIOSConfigUtility worked fine, so the HP TPM – Enable and Activate step application runs:
BiosConfigUtility64.exe /set:TPMSetup.txt
where TPMSetup.txt is:
BIOSConfig 1.0
TPM Device
Hidden
*Available
TPM Activation Policy
F1 to Boot
Allow user to reject
*No prompts
The Take Ownership of TPM runs:
manage-bde.exe -tpm -takeownership NeedsAPassword4321
This now works consistently with the built-in Enable Bitlocker step:
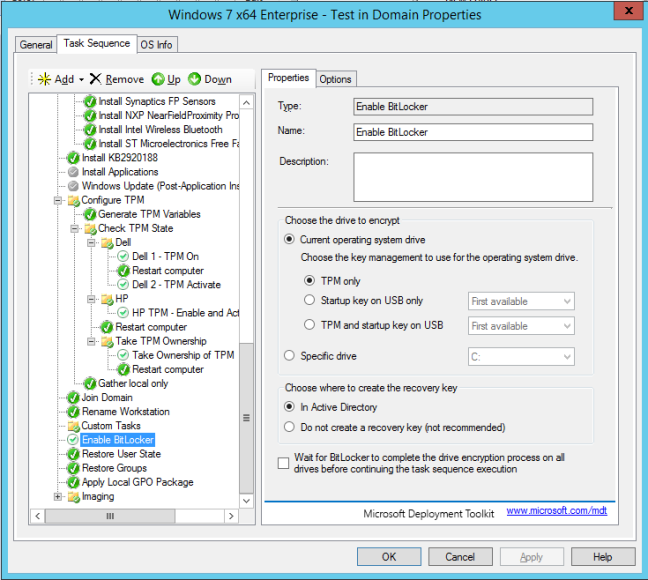
Bitlocker is now enabled. Now to work with the AD folks to get the recovery key into Active Directory…
Links:
Enabling Bitlocker through MDT 2013
https://social.technet.microsoft.com/Forums/en-US/2d3b5694-abcc-4fc3-a8e4-d3a9355c2d44/how-to-enable-the-bitlocker-in-mdt?forum=mdt
Win32_Tpm class
https://msdn.microsoft.com/en-us/library/windows/desktop/aa376484(v=vs.85).aspx
Get-TPMInfo
https://gallery.technet.microsoft.com/Get-TpmInfo-215a8695
Check TPM Status from the Command Line (Enabled | Activated | Owned)
Check TPM Status from the Command Line (Enabled | Activated | Owned)
Nice post – thanks a lot. I wonder why the BIOS PW is set, and then removed twice (once for each TPM section)? It it because you don’t wish to have a PW on the bios after deployment?
LikeLike
Thanks for comment. Yes, we have never set BIOS passwords, and management didn’t want us to start, but since changing the settings required a password to be set, I set a temporary password and then remove it.
LikeLike
Ok thank you for the clarification 🙂
LikeLiked by 1 person
Thanks, Could you please share with us the task sequence.
LikeLike
Hi Ahmed – I don’t have the task sequence anymore… that was 5 years ago at a previous engagement.
LikeLike
Thanks for your reply, do you have any TS that can do dell drivers command update, as well as UEFI and bit locker i would really appreciate
LikeLike
Good morning, Ahmed,
Unfortunately, I do not. Since getting hired for my current position, I have not been involved with OS imaging. That’s handled by a separate team. Good luck!
Terence
LikeLike